Tools
Dridex
Like everybody we receive a lot of spam coming from Dridex dropper samples. That take considerable time to analyse all of them and decoding manualy their bot configuration. Dridex is an old malware now, and we don’t understand why we can’t find a script to decode the configuration, so we made it, and share it =).
Unpack Dridex
Start with this sample: Dridex.exe, md5: c4934e3e1858dbbeb4ea872d0fdbbd79. First step, open it in ollydbg, and put a breakpoint on the VirtualAlloc API:
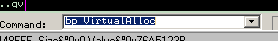
At the second call to VirtualAlloc (this technique run for this sample, for another it can be more or less) put a breakpoint at memory write access in the first byte on the memory address returned by VirtualAlloc. We continue the execution and OllyDBG will break when Dridex starts unpacking its second stage.
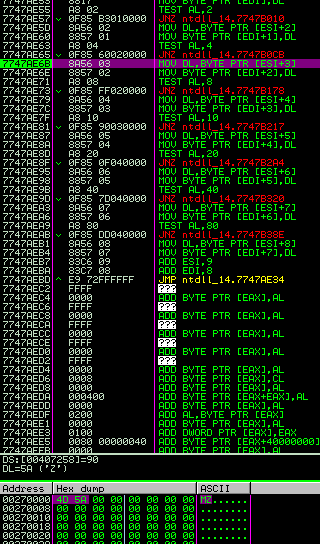
We continue until the end of the decoding routine and we dump the memory region into a file.
s shown below in the screenshoot, the unpacked PE have a sdata section, it is the encrypted bot configuration. The first 4 bytes are the XOR key, the unxored content are compressed by aplib.
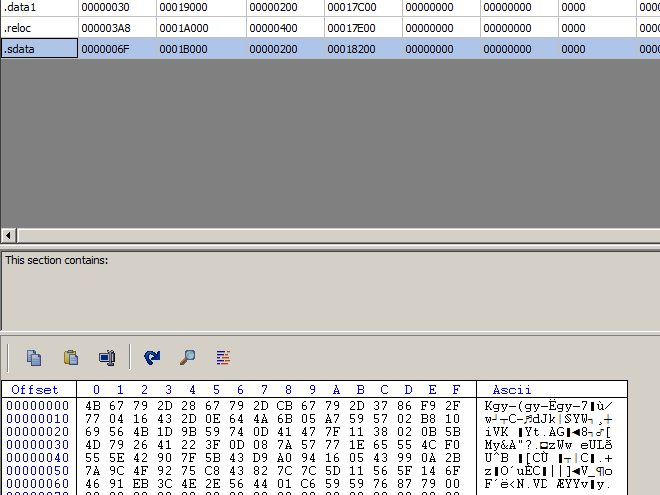
With the Corkami aplib (thank you if you read this =) and pefile python module, it’s easy to automate this boring task.
We launch the script.
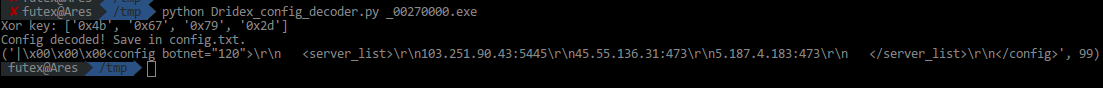
Got it!