Tools
Static analysis
Havex is a well-known RAT. Recently a new plugin appeared and it targets ICS/SCADA systems. We found many different samples. Let’s start by looking at one.
MD5sum: 6bfc42f7cb1364ef0bfd749776ac6d38 6bfc42f7cb1364ef0bfd749776ac6d38
SHA1sum: db8ed2922ba5f81a4d25edb7331ea8c0f0f349ae 6bfc42f7cb1364ef0bfd749776ac6d38
All files are just simple Windows 32-bit DLLs, with no obfuscation, not packed. Nothing creepy! Take a look at the import table.
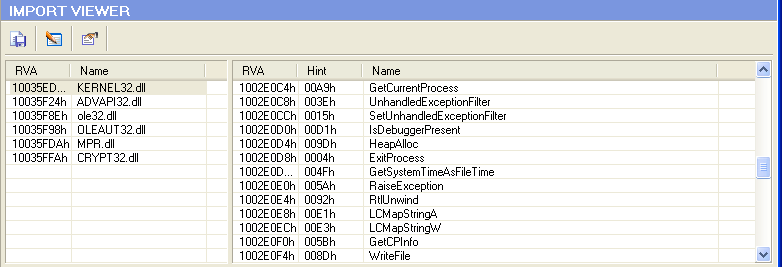
It uses basic anti-debugging tricks (IsDebuggerPresent, GetTickCount…), no winsocket API are call. The most interesting is the import table from MPR.dll.
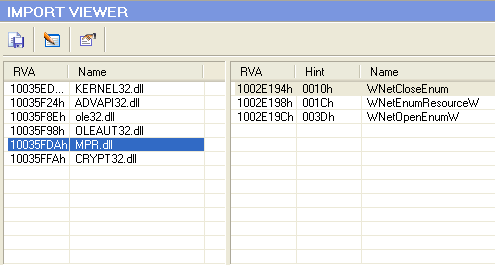
According to the MSDN, WNet* functions are used to enumerate networks resources and connections.
If we look at the Unicode strings, we see clearly something interesting.
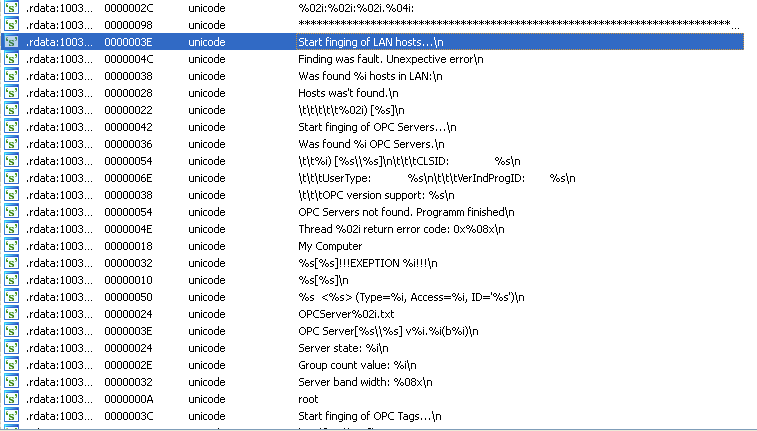
Looking at string’s reference, we find a function that scans the LAN network.
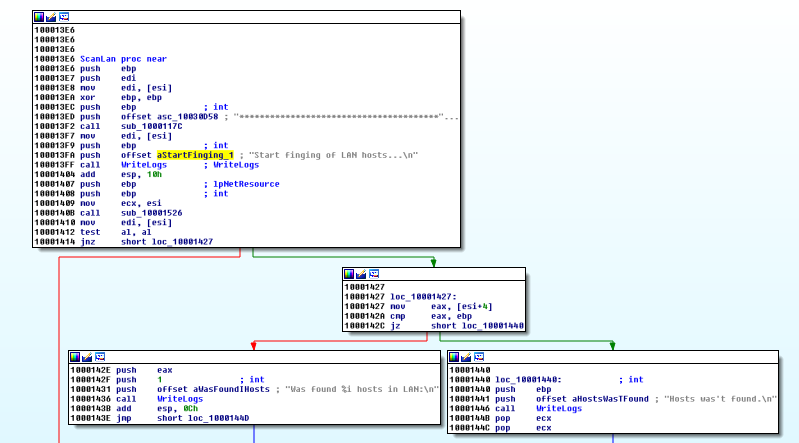
Just after scanning the network, another function that calls WNetEnum* API functions we have seen previously in the import table.
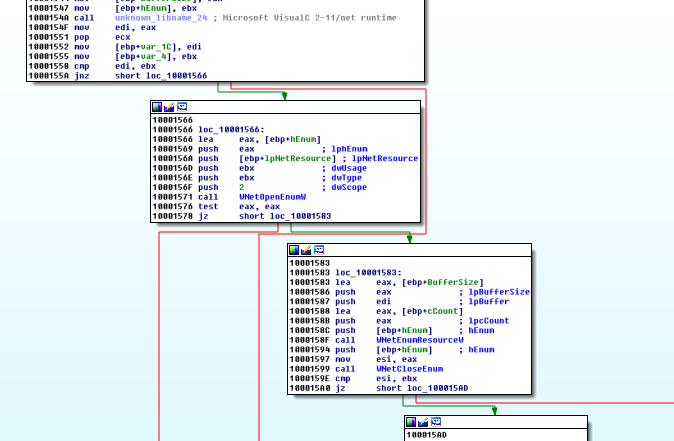
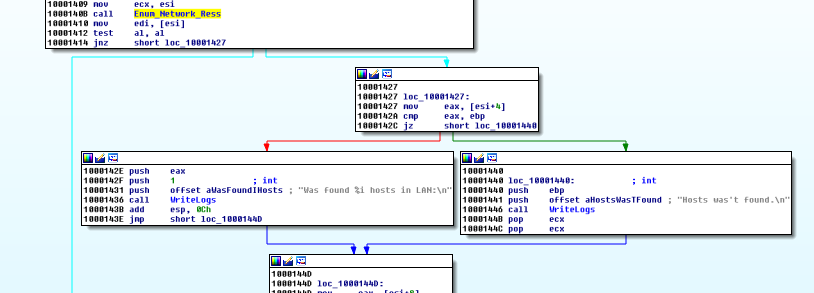
And it calls WriteLogs, as I named it. It writes what it finds into a log file in %TEMP% directory.
After scanning the LAN, more interesting things happen. It is going to scan for OPC servers.
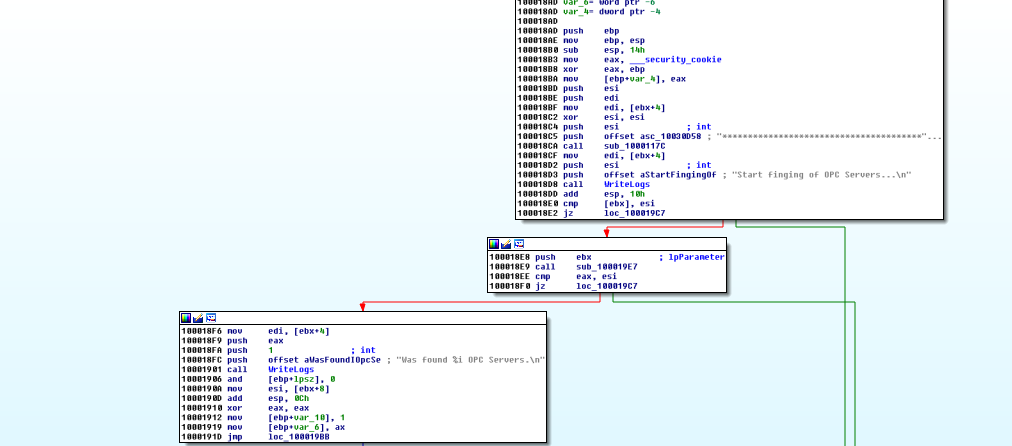
But how can this be done? Look at the sub_100019E7 function: it starts by creating a thread.

It launches COM API functions.
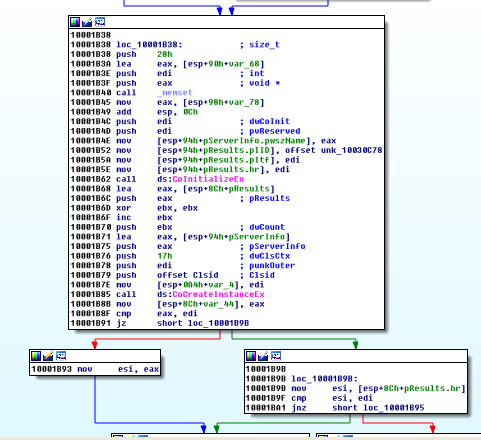
Parameter Unk_10030C70 has the value 9DD0B56C-AD9E-43EE-8305-487F3188BF7A. It is uses to get a list of servers (IID_IOPCServerList2).
Clsid 6C0B50D-09D9-E0AD-0EE4-3835487F31880BF7A is used to retrieve the COM class factory for component (CLSID_OPCServerList).
It searches OPC Tags:
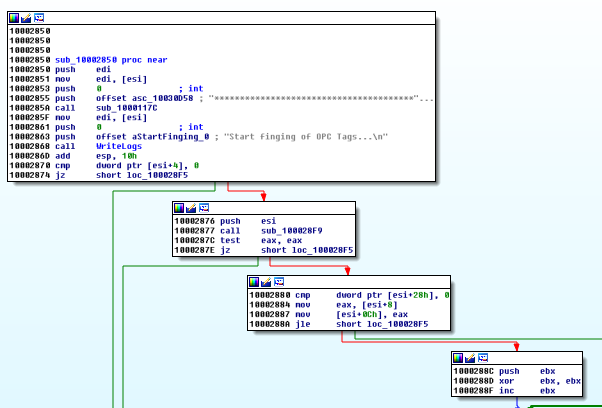
All it finds is written to a file, and sent to the C&C by the RAT.
Conclusion:
This Havex plugin is not difficult to analyse and understand, it does not attack, but is clearly designed to spy industrial networks.
References:
MSDN:
Article: