We wrote an article about the dropper used by Red October available here.
At the end of this article we got a file called svchost.exe and the file wsdktr.ltd . This file was first packed with a custom packer and secondly packed with UPX. Once we unpacked this file, we get a file with the md5: 5f38e180671fe1d86009d730687a0e3e.
This binary is used to decrypt the file wsdktr.ltd.
How to get the .dll stored in wsdktr.ltd
To decrypt the .dll file from xsdktr.ltd we must apply this algorithm:
- a RC4 with the key dfdedkwe3322oeitodkdjeio3e9ekdjwasddcncmvjdasalwpeoryg7534hvn5wewse
- zlib to the result (starting a the byte 4)
Here the screenshot of the initialisation of the RC4 function KSA (function 0x403930):
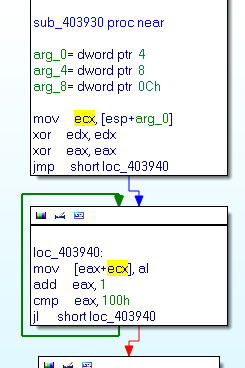
For people who do not recognise RCA init, we can found 2 loops with 256 iterations… (comment for jvoisin)
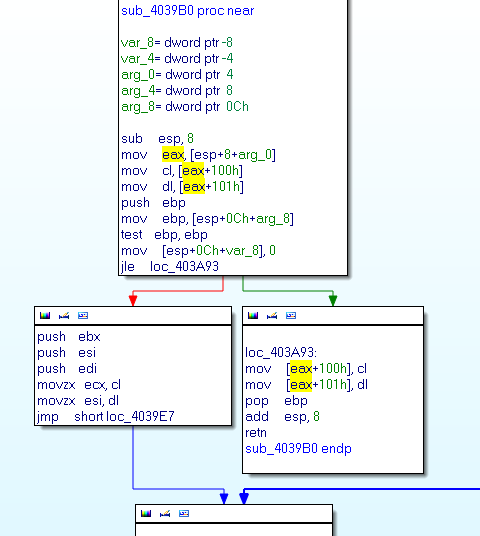
Here the screenshot of the RC4 function PRGA (function 0x4039B0):
Here the usage of the zlib library (function 0x404500):
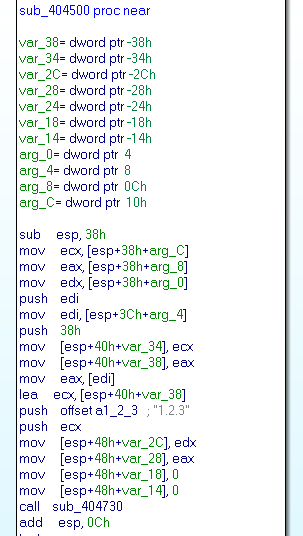
We can identify zlib with some specific strings available in the function.
We develop a script to get the .dll from the wsdktr.ltd file, for information we need to skip the first 4 bytes, these bytes contain the size of the final binary:
#!/bin/python
import sys
from Crypto.Cipher import ARC4
import hashlib
import zlib
key = "dfdedkwe3322oeitodkdjeio3e9ekdjwasddcncmvjdasalwpeoryg7534hvn5wewse"
data = open(sys.argv[1]).read()
rc4 = ARC4.new(key)
decrypted = rc4.encrypt(data)
decompressed = zlib.decompress(decrypted[4:])
sys.stdout.write(decompressed)
The output:
rootbsd@malware.lu:~$ python get_dll.py wsdktr.ltp > final.dll
rootbsd@malware.lu:~$ file final.dll
final.dll: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows, UPX compressed
The .dll md5 is 9b049bcb675377af1ca08fcf3ddad89c.
The unpack .dll md5 is b587fb33613bfbdd2a95e98fc00391d5.
We have (finally) the malware of Red October !!!