Tool and information about the file:
- MD5: 69e83126e526bda1edb44c802d9a1a6c
- SHA1: 282fbb001552b0c587b8cb6ef2148cf81fc32903
- VT detection: https://www.virustotal.com/file/69e83126e526bda1edb44c802d9a1a6c/analysis/
- VT detection ratio: 4 / 41 (04/09/2012)
This article will present how to unpack this specific sample. The methodology uses on this article can be use with several packers that use the heap to decrypt the payload.
Analysis
We start the sample in OllyDBG:
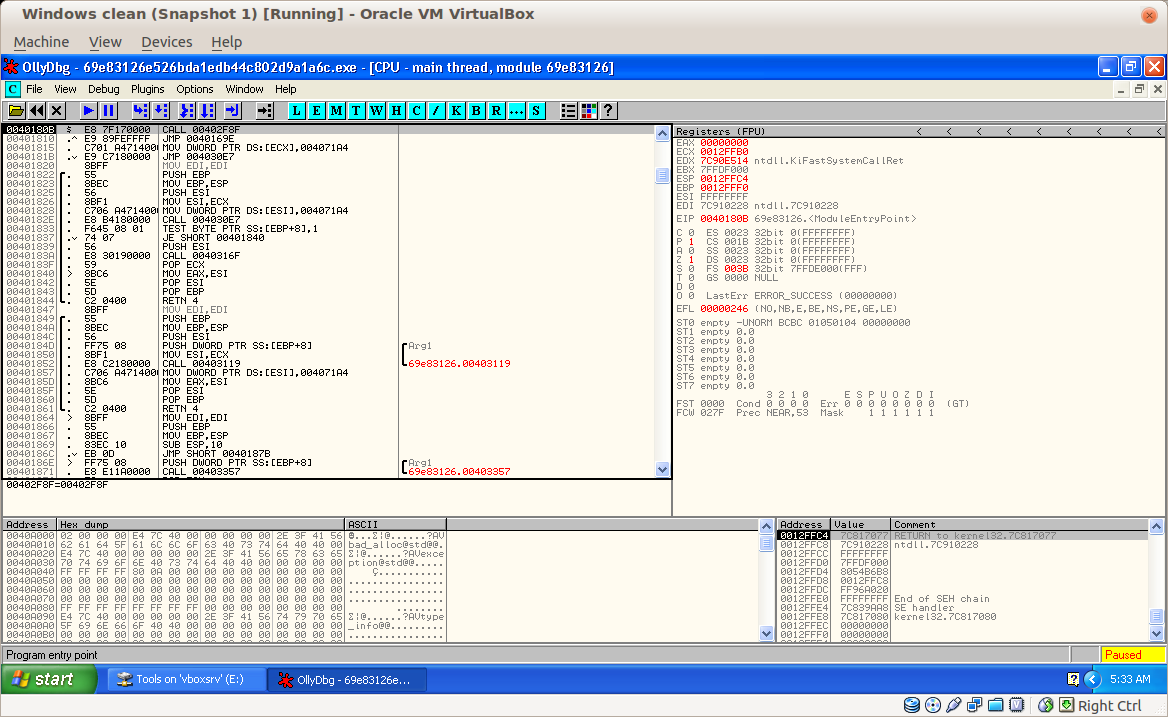
Now, we add breakpoints on VirtualAlloc function by clicking on View -> Executable modules :
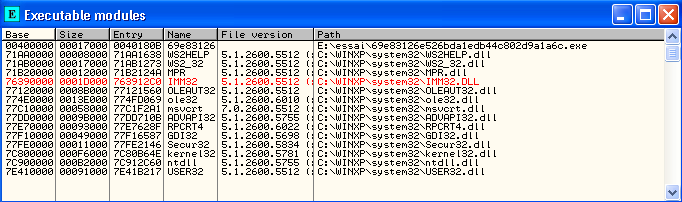
Right-click on kernel32.dll et click to View Names.
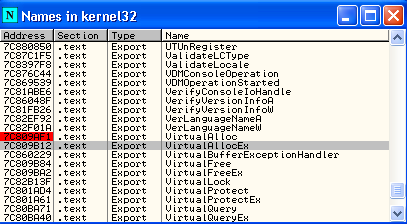
Press F2 (add breakpoint) on VirtualAlloc line.
Now we can run the application with F9.
The application stop on a first VirtualAlloc:
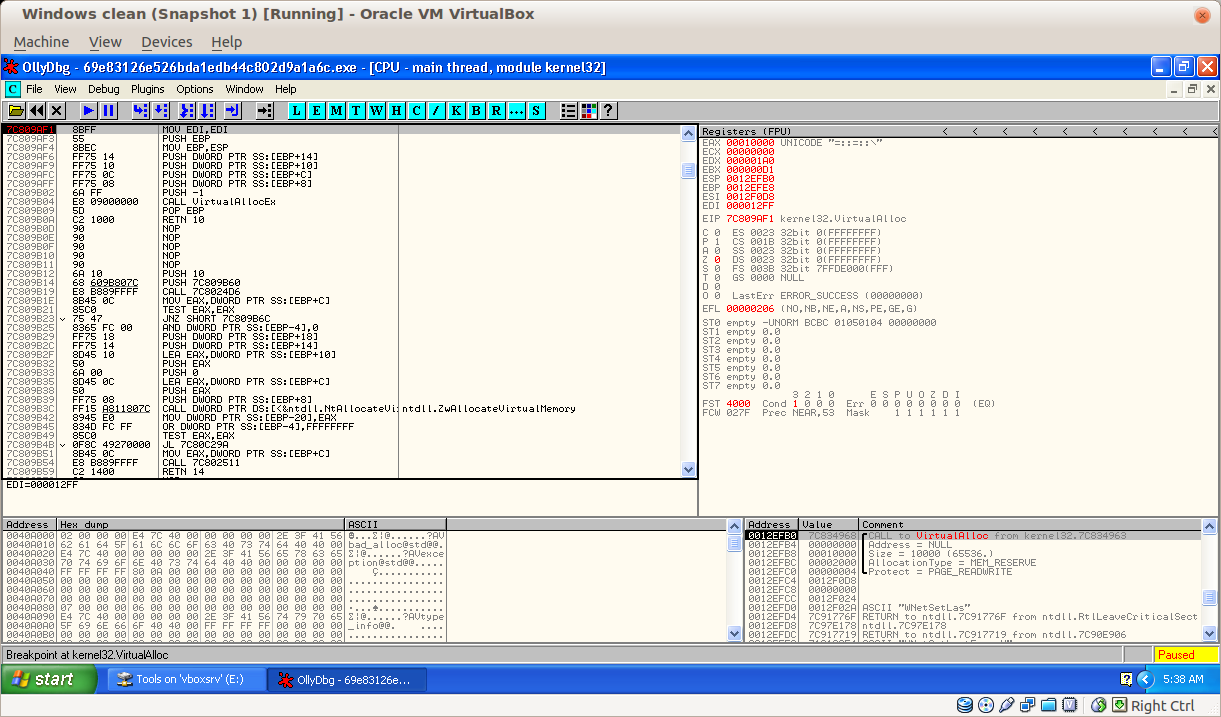
Press Control+F9 to go at the end of the VirtualAlloc function. We can see the value of the memory allocated by the function in EAX: 0xAF0000.
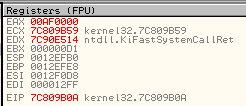
We add a breakpoint on write access on the memory section. To add the breakpoint, we press Ctlr+F9 to leave the function and go to View -> Memory :
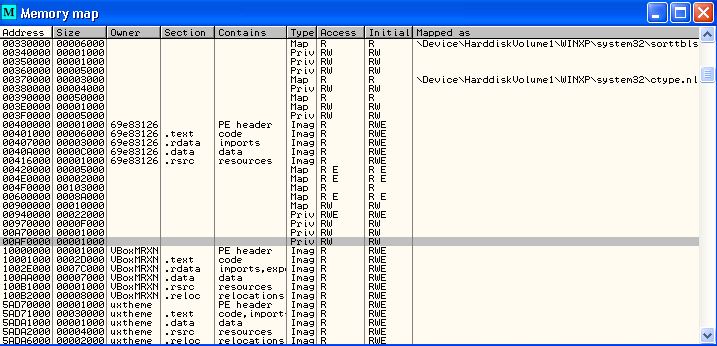
Right-click on the memory address (0xAF0000) and Set memory breakpoint on write. Press F9 to continue the execution.
The application stop at 0x940ACA, because the memory region 0xAF0000 was access in write (Memory breakpoint when writing to 00AF0000):
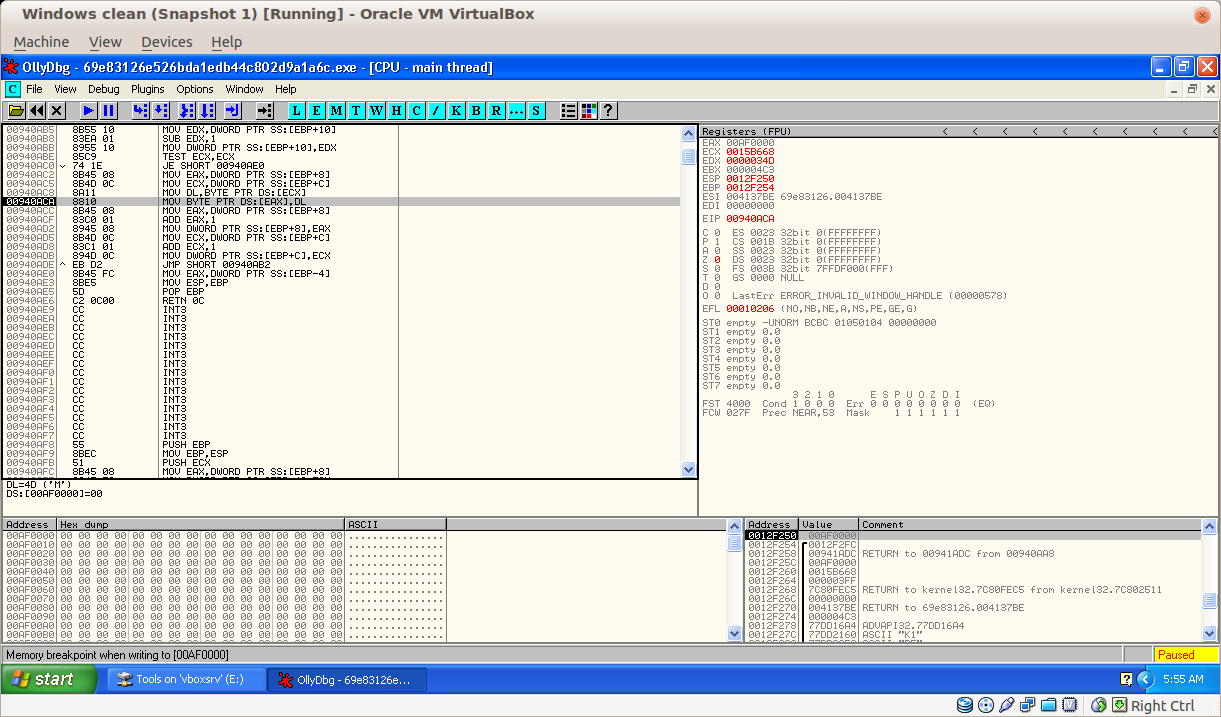
The ASM code is :
MOV DL, BYTE PTR DS:[ECX]
MOV BYTE PTR DS:[EAX], DL
EAX=0xAF0000 and ECX=0x15B668
ECX is the source of the copy, right-click on the value (0x15B668) and click on Follow the dump:
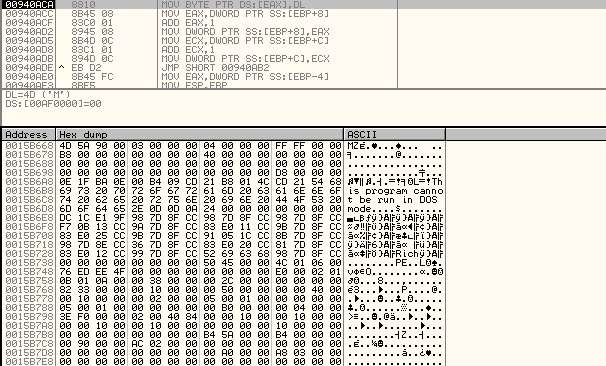
A MZ is available at 0x15B668. We can dump it with right-click -> Backup -> Save data to file. The file generated is a full dump of the memory region. We must cut the file at the good offset:
rootbsd@malware.lu:~$ grep -aobn MZ _00150000.exe
45:46696:MZ
57:51960:MZ
57:52514:MZ
59:54737:MZ
72:63343:MZ
rootbsd@malware.lu:~$ tail -c+46697 _00150000.exe > final.exe
The final.exe binary is the unpack file.
rootbsd@malware.lu:~$ file final.exe
final.exe: PE32 executable (GUI) Intel 80386, for MS Windows
rootbsd@malware.lu:~$ md5sum final.exe
1d0d2d33ef6d3783f0edb01339ca0742 final.exe