We are going to explain how we unpack the sample 3798a387a7d2cb9d623b68cb13aa60fd packed with a unknown packer.
Virus information:
- MD5: 3798a387a7d2cb9d623b68cb13aa60fd
VT
Detection ratio: 1/35 Report VT
Yara
Nothing with yara and packer rules
y0ug@laptop:~$ yara-pack 3798a387a7d2cb9d623b68cb13aa60fd
y0ug@laptop:~$
Unpack
We decide to unpack the sample with OllyDbg, we open the sample and we are in this situation: 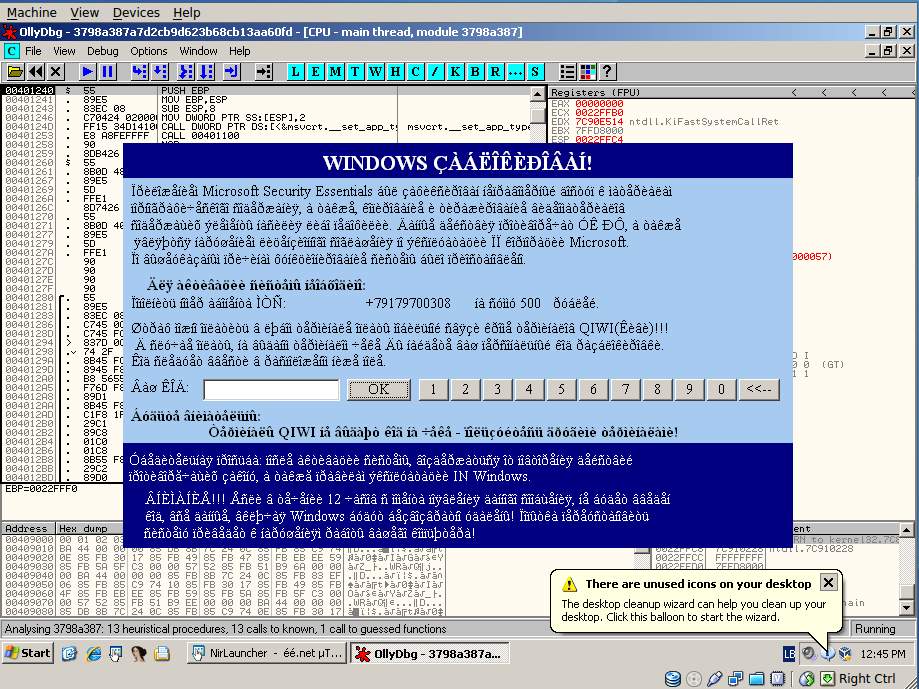
OllyDbg does not stop on the entry point of the program and executes directly the malware. It locks the workstation, so we can do nothing.
We take a look on the OllyDbg option and find this one:
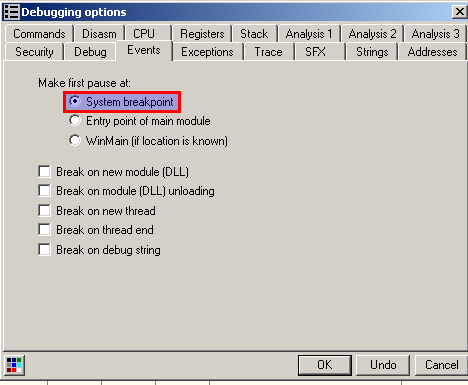
This option tells to OllyDbg to set the first pause when the system load the binary.
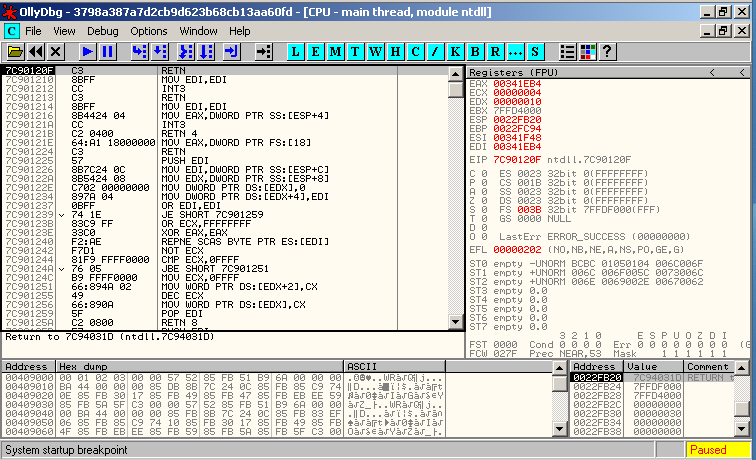
We run the sample with the option set. The programme break in the ntdll.dll
We suspect that the packer is a heap packer, so we define some breakpoints on functions of kernel32.dll that know to be used by heap packer.
To set these breakpoints we have to show “Executable Module”, right click on kernel32.dll and click on “view names”
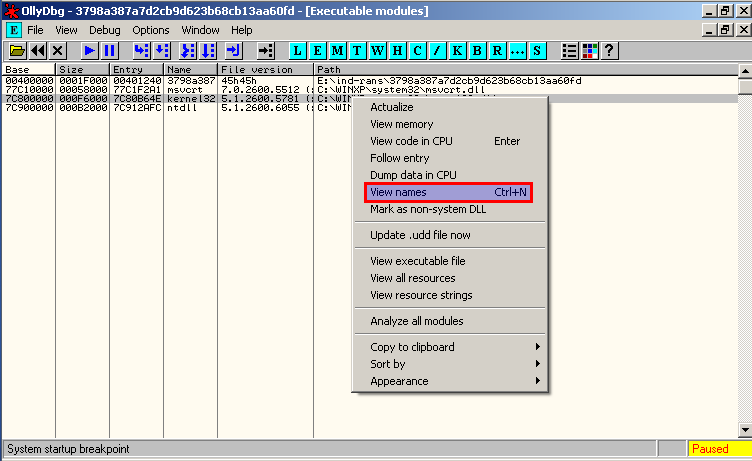
And we define the breakpoints by selected the functions and press F2
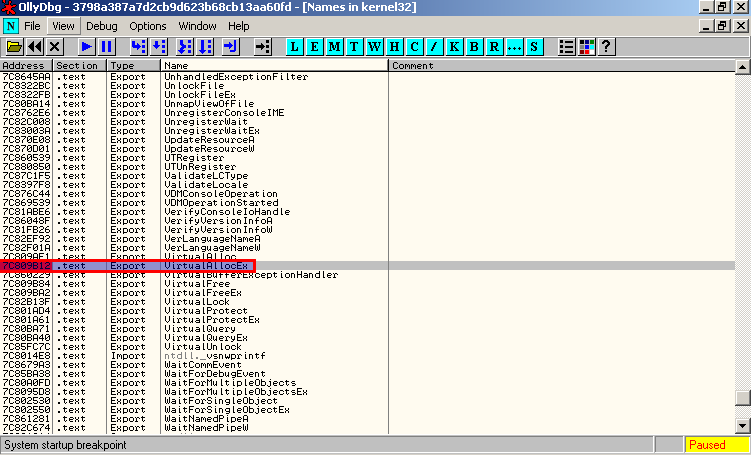
We repeat this task for:
- VirtualAllocEx
- WriteProcessMemory
- OpenProcess
- CreateProcess
- CreateRemoteThread
We press run. The execution break on CreateProcess, 2 VirtualAlloc and WriteProcessMemory.
WriteProcessMemory is the breakpoint which is interesting.
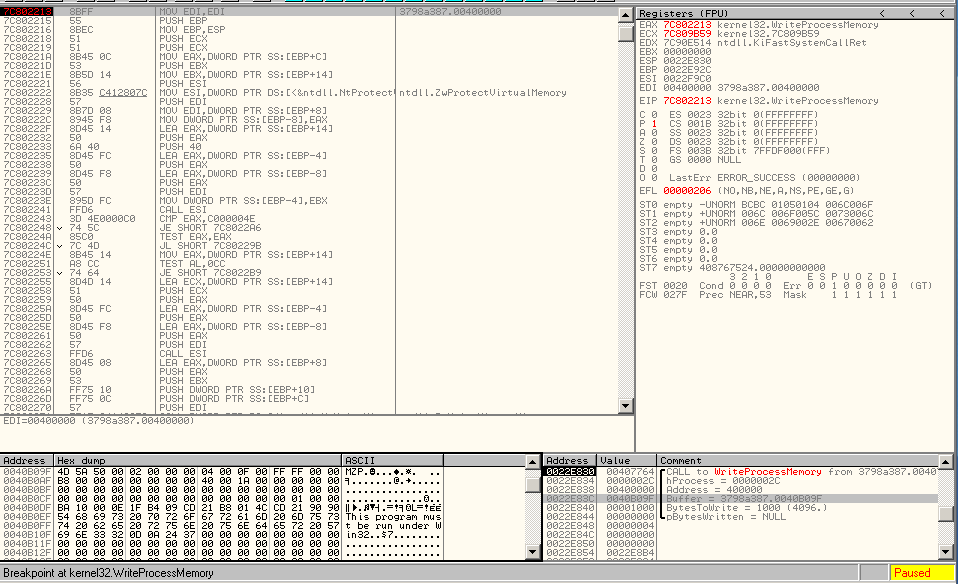
We look at the buffer address and we show the address in the dump.
We notice the MZ bytes and dump the page.
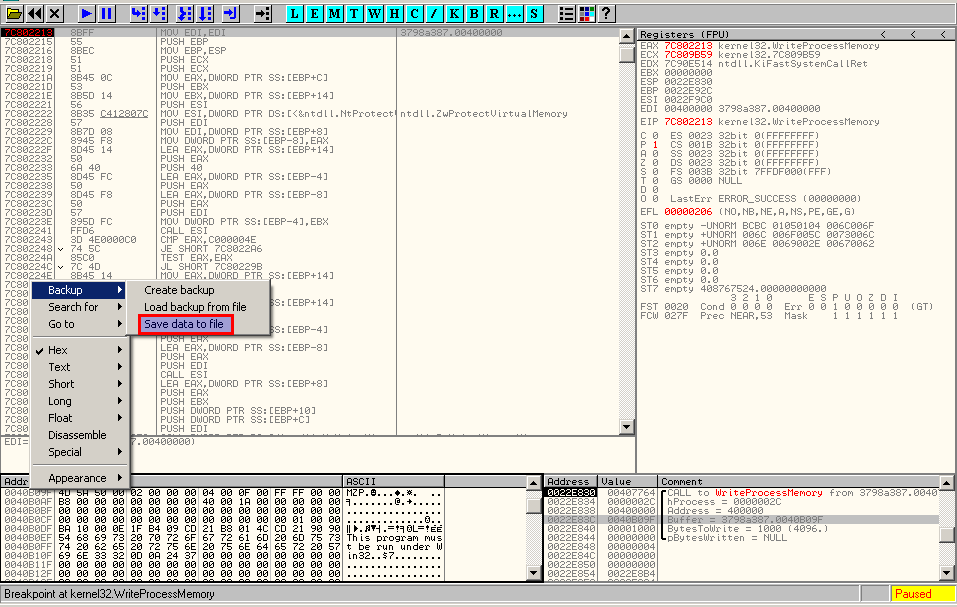
We extract the binary from the dump
y0ug@laptop:~$ pcalc 0x0040b09f - 0x00409000
8351 0x209f 0y10000010011111
y0ug@laptop:~$ tail -c+8352 3798a387a7d2cb9d623b68cb13aa60f_00409000.bin > 3798a387a7d2cb9d623b68cb13aa60f.u.exe
y0ug@laptop:~$ file 3798a387a7d2cb9d623b68cb13aa60f.u.exe
3798a387a7d2cb9d623b68cb13aa60f.u.exe: PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed
y0ug@laptop:~$ upx -d 3798a387a7d2cb9d623b68cb13aa60f.u.exe
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2011
UPX 3.08 Markus Oberhumer, Laszlo Molnar & John Reiser Dec 12th 2011
File size Ratio Format Name
-------------------- ------ ----------- -----------
121697 <- 57185 46.99% win32/pe 3798a387a7d2cb9d623b68cb13aa60f.u.exe
Unpacked 1 file.
y0ug@laptop:~/ShareVM/ind-rans$ md5sum 3798a387a7d2cb9d623b68cb13aa60f.u.exe
a52d3e4cbf11b32ae277c3ca0c9df17b 3798a387a7d2cb9d623b68cb13aa60f.u.exe
Malware analysis
The malware is wrote in delphi and the md5 is a52d3e4cbf11b32ae277c3ca0c9df17b
VT
Detection ratio: 10/42
Conclusion
We do not make a static analysis of the sample, but with the sandbox report we find, is a win locker:
- is persistant by updating this reg key:
HKU\S-1-5-21-842925246-1425521274-308236825-500\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
HKU\S-1-5-21-842925246-1425521274-308236825-500\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- changes some reg key in HKLM\System\CurrentControlSet\Control\SafeBoot\M\ to disable the safe mode.