We received an email with an invoice from Apple (in french).
Of course we never bought something from Apple!!!!
The link of the invoice seems to be : http://www.apple.com/clients/download/facture50522231823v.zip
But when we put our mouse on the link we can see the real link: http://editionslabonte.com/plugins/Facture147778.zip
We think that the Website “editionslabonte.com” was compromised and the attacker puts the malware on it. We sent an email to the administrator and we do not have a feedback for the moment.
Tools
- A debugger for dynamic analysis (in our case OllyDbg)
- LordPE in order to dump a memory page
- Volatility in order to analyse memory dump
Zip archive
The md5 of the archive is e0aa33dc57aa3eee43cb61933eb3241c.
Virustotal score : 5/42
So we downloaded the .zip file.
rootbsd@alien:~/Samples$ unzip -l Facture147778.zip
Archive: Facture147778.zip
Length Date Time Name
--------- ---------- ----- ----
176128 2012-07-14 03:05 Facture147778.pdf .scr
--------- -------
176128 1 file
The .zip contains one file. To trick the user, the attacker adds several space before the extension .scr, some users may thought that the file is really a .pdf.
First binary
rootbsd@alien:~/Samples$ yara -r packer.yara Facture147778.pdf\ \ \ \ \ \ \ \ \ \ \ \ .scr
java Facture147778.pdf .scr
NETexecutableMicrosoft Facture147778.pdf .scr
The file is a .NET binary.
With the strings command, we find somethink that looks like a base64.
We extract the base64 :
rootbsd@alien:~/Samples$ cat base64.dmp
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAA4AAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1v
ZGUuDQ0KJAAAAAAAAACZtmjHqtcGlN3XBpTd1waUpssKlNzXBpReywiU3NcGlDXIDJTW1waUNcgC
lNnXBpQe2FuU1NcGlN3XB5Tg1waUNcgNlNzXBpRl0QCU3NcGlFJpY2jd1waUAAAAAAAAAABQRQAA
TAEEAKYPc0oAAAAAAAAAAOAADwELAQYAAEIAAACUAAAAAAAAdE8AAAAQAAAAYAAAAABAAAAQAAAA
AgAABAAAAAAAAAAEAAAAAAAAAAAQAQAABAAAAAAAAAIAAAAAABAAABAAAAAAEAAAEAAAAAAAABAA
[...]
W1EPulAAAAIAAQAgAEAAAQABADQBAAAFAAAAAQAEACAgEAABAAQA6AIAAAEAEBAQAAEABAAoAQAA
AgAgIAAAAQAgAKgQAAADABAQAAABACAAaAQAAAMAUEEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAA=
We decode this file.
rootbsd@alien:~/Samples$ cat base64.dmp | base64 -d > base64.out
rootbsd@alien:~/Samples$ file base64.out
base64.out: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
This base64 is a PE32 executable.
Second binary
We use yara to identify the binary:
rootbsd@alien:~/Samples$ yara -r packer.yara base64.out
rootbsd@alien:~/Samples$
This binary doesn’t use a well-known packer. So we decided to unpack it manually.
To unpack it, we use OllyDBG.
We are suprised by a lot of exception when we tried to debug the sample.
In fact this malware volontary uses and traps exceptions to be unpacked.
So as usual, we add breakpoint on VirtualAlloc & VirtualAllocEx calls:
-
View
-
Executable modules
-
right click on kernel32.dll -> View names
-
F2 on VirtualAlloc & VirtualAllocEx
Now we run the malware with F9
A lot of exception must be pass. Use shift+F9 to pass it.
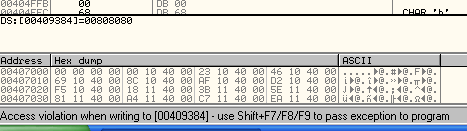
Now the application is break at kernel32.VirtualAllocEx :
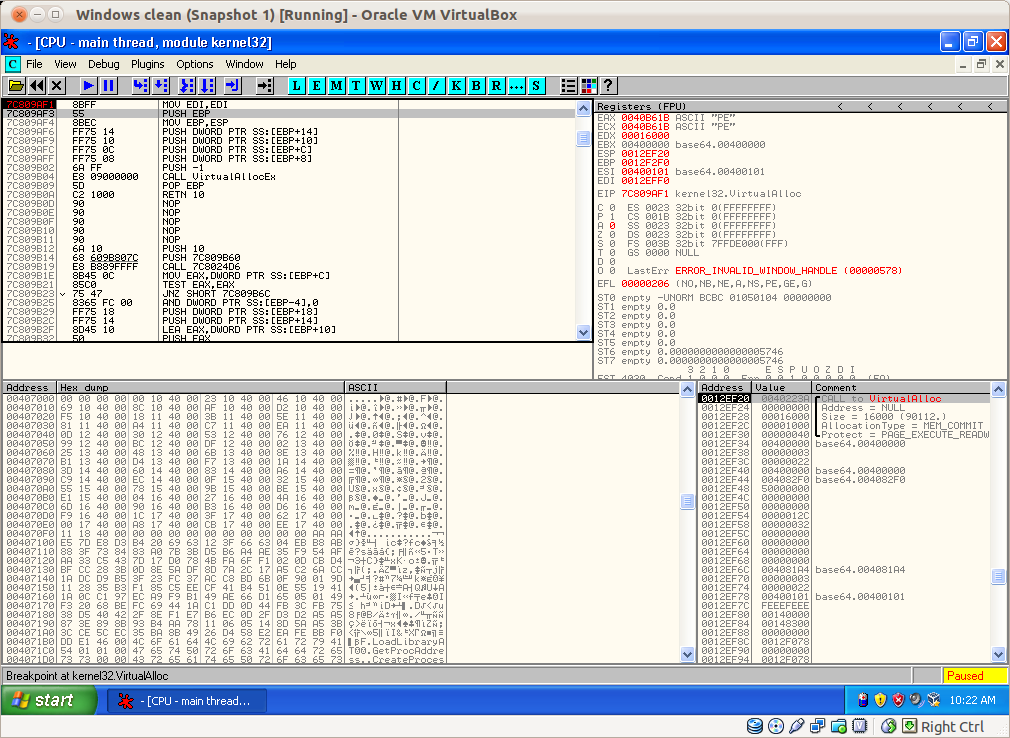
Execute the binary until the next RET with Ctrl+F9.
Now we can see the allocated address of the memory in the EAX register: 0x40B61B.

Right click on the EAX value, and click on “Follow in dump”.
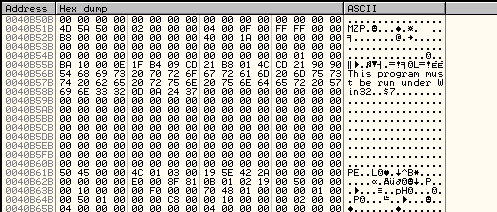
We can see a PE value in the bottom left. If we scroll we can see the complete MZ :
Now we can use lordPE to make a partial dump: - launch LordPE
-
right click on the process
-
Dump partial
-
set the start address to 40B51B
-
set the size to 411000 - 40B51B = 5AE5
Now we have a binary with the md5: 18e5ff1d0610341257f33e6fefe4f9a7
Third binary
We used yara to identify the binary:
rootbsd@alien:~/Samples$ yara -r packer.yara base64.stage2.dmp
UPXv20MarkusLaszloReiser base64.stage2.dmp
UPXV200V290MarkusOberhumerLaszloMolnarJohnReiser base64.stage2.dmp
UPX20030XMarkusOberhumerLaszloMolnarJohnReiser base64.stage2.dmp
The binary is simply pack with UPX.
rootbsd@alien:~/Samples$ upx -o base64.stage2.exe -d base64.stage2.dmp
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2010
UPX 3.07 Markus Oberhumer, Laszlo Molnar & John Reiser Sep 08th 2010
File size Ratio Format Name
-------------------- ------ ----------- -----------
46821 <- 23269 49.70% win32/pe base64.stage2.exe
Unpacked 1 file.
rootbsd@alien:~/Samples$ file base64.stage2.exe
base64.stage2.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit
We have got the final binary.
Fourth binary
We easily identify a well-known RAT:
rootbsd@alien:~/Samples$ strings -el base64.stage2.exe | grep RAT
Xtreme RAT SOFTWARE\XtremeRAT
After a quick search on Google, we discovered that the RAT could be buy here: https://sites.google.com/site/nxtremerat/.
The second interesting think is that fact that the RAT is used in Syria : https://www.eff.org/deeplinks/2012/03/how-find-syrian-government-malware-your-computer-and-remove-it/
We can use 3 methods to analyse the binary: the simple, the semi talented method and the full talented method.
Simple
We execute it, and launch netstat.exe on Windows. The IP of the C&C is 41.103.186.12 and port 2013.
It’s an IP from Alger:
rootbsd@alien:~/Samples$ whois 41.103.186.12
% This is the AfriNIC Whois server.
% Note: this output has been filtered.
%Information related to '41.103.0.0 - 41.103.255.255'
inetnum: 41.103.0.0 - 41.103.255.255
netname: RegAlg1
descr: Region Alger 1
country: DZ
admin-c: SD6-AFRINIC
tech-c: SD6-AFRINIC
status: ASSIGNED PA
mnt-by: DJAWEB-MNT
source: AFRINIC # Filtered
parent: 41.96.0.0 - 41.111.255.255
person: Security Departement
address: Alger
phone: +21321922004
fax-no: +21321922004
e-mail: security@djaweb.dz
nic-hdl: SD6-AFRINIC
source: AFRINIC # Filtered
To be persitent, the malware adds a value (antivirus) in the registry: Software\Microsoft\Windows\CurrentVersion\Run
The malware is stored in the directory: C:\Windows\Browser\Web.exe
A configuration file is available here: C:\Documents and Settings\rootbsd\Application Data\Microsoft\Windows\S5tVn.cfg
Semi talented
We can use a memory dump to analyse the binary. We use volatility to analyse the binary:
rootbsd@alien:~/Samples$ volatility/vol.py -f output pslist
Volatile Systems Volatility Framework 2.0
Offset(V) Name PID PPID Thds Hnds Time
---------- -------------------- ------ ------ ------ ------ -------------------
0x812ed020 System 4 0 54 247 1970-01-01 00:00:00
0xffbaeb10 smss.exe 368 4 3 19 2012-05-21 15:20:54
0x811248e0 csrss.exe 584 368 10 379 2012-05-21 15:20:54
0x81197248 winlogon.exe 608 368 21 514 2012-05-21 15:20:54
0x811275a8 services.exe 652 608 16 253 2012-05-21 15:20:54
0x8112d7e0 lsass.exe 664 608 23 338 2012-05-21 15:20:54
0xffbd7a78 VBoxService.exe 820 652 8 106 2012-05-21 15:20:54
0x81180c30 svchost.exe 864 652 19 197 2012-05-21 06:20:56
0x811a6b28 svchost.exe 952 652 9 237 2012-05-21 06:20:56
0xffac4218 svchost.exe 1044 652 79 1367 2012-05-21 06:20:56
0xffabbd08 svchost.exe 1092 652 6 76 2012-05-21 06:20:56
0x8116cda0 svchost.exe 1132 652 13 172 2012-05-21 06:20:56
0x8112eca8 spoolsv.exe 1544 652 14 111 2012-05-21 06:20:57
0xffa93b00 explorer.exe 1556 1504 17 477 2012-05-21 06:20:57
0x8112fda0 VBoxTray.exe 1700 1556 6 58 2012-05-21 06:20:57
0xffb95da0 svchost.exe 1904 652 4 106 2012-05-21 06:21:05
0xffa01a98 alg.exe 1076 652 6 107 2012-05-21 06:21:09
0x81178278 wscntfy.exe 1188 1044 1 31 2012-05-21 06:21:11
0x81188da0 wuauclt.exe 1956 1044 8 180 2012-05-21 06:21:51
0x811323c0 wuauclt.exe 248 1044 4 133 2012-05-21 06:22:05
0x8119ada0 svchost.exe 2000 1488 2 41 2012-07-20 19:15:47
0x8118b888 svchost.exe 1404 1488 8 188 2012-07-20 19:15:47
The 2 last svchost.exe are stange. The date is not logic.
When you list the dll you can see that the malware change his name to svchost.exe:
rootbsd@alien:~/Samples$ ../Pentest/volatility/vol.py -f output -p 2000 dlllist
Volatile Systems Volatility Framework 2.0
************************************************************************
svchost.exe pid: 2000
Command line : svchost.exe
Service Pack 3
Base Size Path
0x00400000 0x038000 E:\essai\svchost.exe
0x7c900000 0x0b2000 C:\WINXP\system32\ntdll.dll
0x7c800000 0x0f6000 C:\WINXP\system32\kernel32.dll
0x7e410000 0x091000 C:\WINXP\system32\user32.dll
0x77f10000 0x049000 C:\WINXP\system32\GDI32.dll
0x76390000 0x01d000 C:\WINXP\system32\IMM32.DLL
0x77dd0000 0x09b000 C:\WINXP\system32\ADVAPI32.dll
0x77e70000 0x093000 C:\WINXP\system32\RPCRT4.dll
0x77fe0000 0x011000 C:\WINXP\system32\Secur32.dll
0x7c9c0000 0x818000 C:\WINXP\system32\shell32.dll
0x77c10000 0x058000 C:\WINXP\system32\msvcrt.dll
0x77f60000 0x076000 C:\WINXP\system32\SHLWAPI.dll
0x773d0000 0x103000 C:\WINXP\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.6028_x-ww_61e65202\comctl32.dll
0x5d090000 0x09a000 C:\WINXP\system32\comctl32.dll
We make a memory dump of the process 1404 :
rootbsd@alien:~/Samples$ volatility/vol.py -f output -p 1404 memdump -D .
Volatile Systems Volatility Framework 2.0
************************************************************************
Writing svchost.exe [ 1404] to 1404.dmp
In the .dmp we have got all necessary information:
rootbsd@alien:~/Samples$ strings -a 1404.dmp | grep http://
[...]
http://baloobadjamel.hopto.org:2013/1234567890.functions
[...]
rootbsd@alien:~/Samples$ nslookup baloobadjamel.hopto.org
Server: 192.168.0.254
Address: 192.168.0.254#53
Non-authoritative answer:
Name: baloobadjamel.hopto.org
Address: 41.103.186.12
And we find the IP.
We hope that Djamel Baloodad is not the real name of the owner of the C&C ;)
Talented
We open the final binary on IDA.
To help us you can find the .idb here
At loc_C889C9, we find two functions sub_C93B1C (loadConfigResource) and sub_C82914 (decondeConfig).
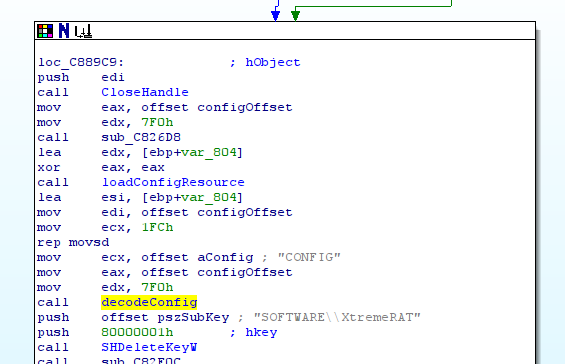
The fisrt function extracts a resource. This resource is the config file (in this case S5tVn.cfg).
The second function decode the configuration file. Two interesting arguments are passed ton the function: the offset of the config file & the word “CONFIG” (in unicode).
This function is composed of 3 loops. This kind of layout looks like RC4 (RC4) :
The first loop:
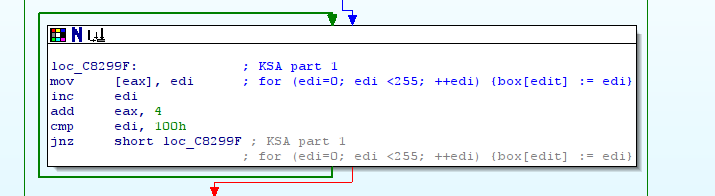
The second loop:
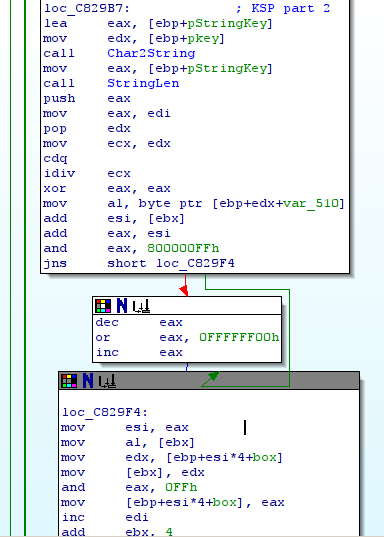
And the final loop:
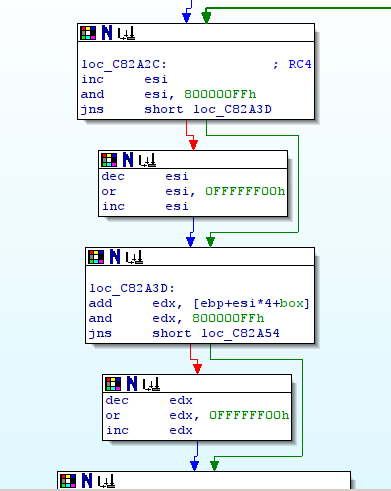
So the config file is crypted with RC4 with the key “CONFIG”.
To perform a RC4 encryption we need the length of the key. To have this size the developer mades his own function sub_C81AF8 (StringLen) but this function does not support unicode, it returns 6 and not 12. So we must implemente this bug in our tool to decrypt the config file.
A script to decode the config file is available here
rootbsd@alien:~/Samples$ ./xtremerat_config.py xtreme.exe | strings -el
baloobadjamel.hopto.org
Spam2013
teSpam2013
Web.exe
Browser
svchost.exe
Antivirus
Antivirus
P8CWY65J-GY7I-CD3S-7K6Q-BD3A60R037L3
Server
3.5 Private
S5tVn
S5tVnEXIT
S5tVnPERSIST
ftp.ftpserver.com
pData\Local
ftpuser
ftppass
Error
ivateAn unexpected error occurred when starting the program.
Please try again later.
We can already see the C&C, the port, etc…
We are working on the format on the configuration file, for the moment we identify this format:
rootbsd@alien:~/Samples$ ./xtremerat_config.py -d xtreme.exe
name10: 3.5 PrivateS5tV
name11: st�S5tVnEXI
name6: Antivirus
name7: Antivirus
host: baloobadjamel.hopto.org
num: 101
name2: teSpam2013
name3: Web.exe
port: 2013
name8: P8CWY65J-GY7I-CD3S-7K6Q-BD3A60R037L3
name9: Server
name: Spam2013
name4: Browser
name5: svchost.exe