We currently work on a ASM ripper in ruby. The purpose is to execute directly ASM code extract from a binary (usefull for decoder/decrypter)
To perform this work we decided to use metasm that is a cross-architecture assembler, disassembler, compiler, linker and debugger write in Ruby : http://code.google.com/p/metasm/
The code source of our ripper is available here
Example
To show how the ripper works we will use the herpesnet decoder.
The encoded strings are submited to a decoder function (0x403034):
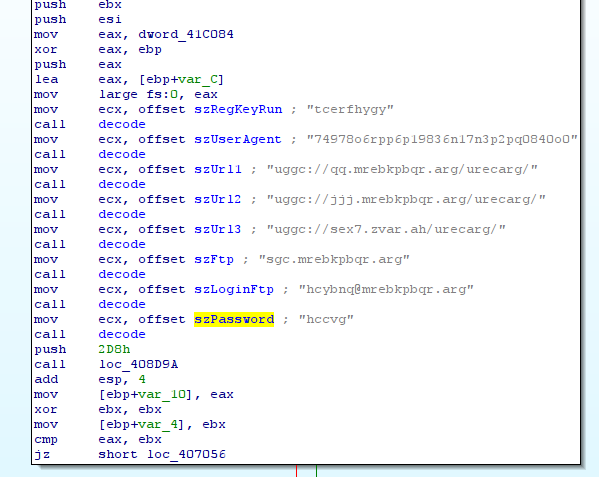
The encoded strings are stored in ecx. The function uses to decode string:
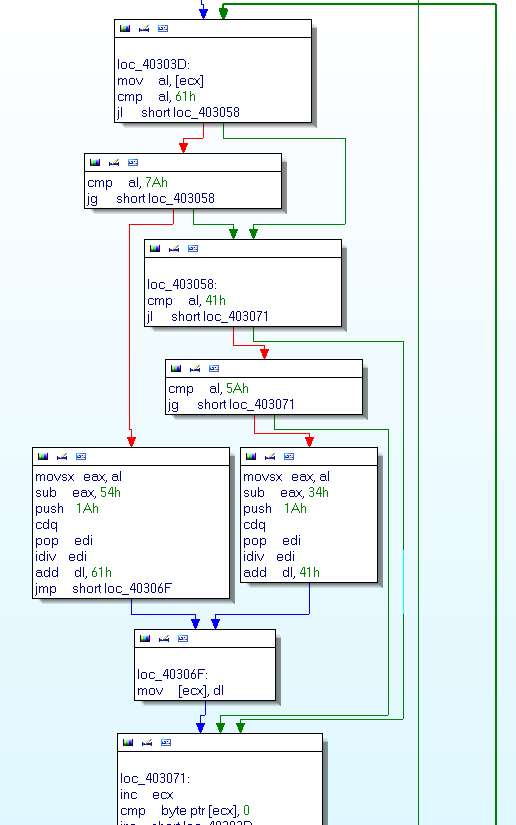
So we do not try to understand the ASM code but only use it… The code source of the ripper:
#!/usr/bin/env ruby
# include the magic ripper
require "ripper.rb"
# a loop to get each encoded string
for a in [ 0x1AE88, 0x1AEF0, 0x1AF54, 0x1AF88, 0x1AFEC, 0x1B020, 0x1B084, 0x1B0B8, 0x1B0EC, 0x1B120, 0x1B184 ]
srcFile = File.open(ARGV[0], 'r')
srcFile.seek(a, IO::SEEK_SET)
string = srcFile.sysread(0x20)
# ARGV[0] in the binary to rip
# 0x403034 is the adress of the function use to decode string
# "unsigned int decode();" is the prototype of the function decode()
# each [], [], [], [] are not used in this example
# string contain the encoded string and must be store in ecx
specs = [Spec.new(ARGV[0], 0x403034,"unsigned int decode();", [], [], [], [], string)]
worker = Ripper.new(specs)
worker.runner.decode()
puts string
end
You can add a 1 to the Ripper.new() to get a vi on the ASM and manualy edit it ;)
So you rip & execute an ASM function in 3 lines of ruby !!!
rootbsd@malware.lu$ ./decode.rb db6779d497cb5e22697106e26eebfaa8
gpresultl
http://dd.zeroxcode.net/herpnet/
74978b6ecc6c19836a17a3c2cd0840b0
http://www.zeroxcode.net/herpnet
ftp.zeroxcode.net
http://frk7.mine.nu/herpnet/
upload@zeroxcode.net
uppit
hwfqfqooatstwuuhhtstshwq
esstttubbb
Nfusheapfzk